USA Computer Services Blog
Technology can do some incredible things, but there’s a reason why basic tools still remain popular even to this day. It’s because they cracked the code for productivity, and they are so easy that anyone can use them. For example, there’s the Cut, Copy, and Paste commands that can be used in literally any application out there.
McAfee recently released a list of 15 applications the company identified as “predatory loan apps” available for download from the Google Play Store. While steps have been taken to remove them from the platform, we can now discuss how mobile applications can be weaponized if a user is not careful.
Let’s start by discussing the current issue of SpyLoan apps.
With so much of the world now online, it’s no wonder that advertisers have shoveled countless dollars into embedded advertisements. Whether you’re reading articles, watching videos, or even scrolling through your social media feed, it’s expected that ads are a part of that experience—even though most people find them to be disruptive, annoying, and invasive. Many users have resorted to ad blockers in an attempt to make the Internet bearable.
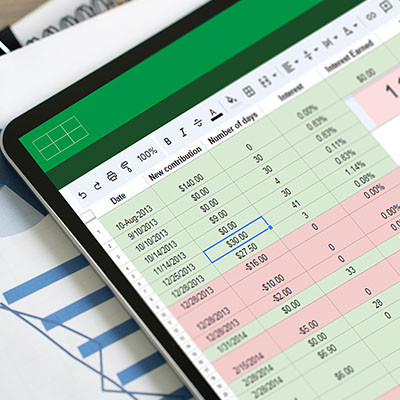
Handling time calculations in a spreadsheet can often feel frustrating—especially when you’re just trying to add them up. Luckily, both Microsoft Excel and Google Sheets have built-in functions specifically designed for this purpose, making the process more manageable.
Here’s a quick guide to help you get started, no matter which spreadsheet program you use.
You can’t run a modern business without software. Even your most basic solopreneur business runs using software at its foundation. For businesses, this problem is increased dramatically as the amount of software fueling operations increases. Software management tools can improve the way your organization keeps tabs on its software.
Your business depends on technology, but it’s rare that all employees at an organization understand the importance of it. More often than not, technology is so ingrained into operations that employees can get overwhelmed by it. Today, we want to share three top tips that will help your employees better understand the technology they use on a day-to-day basis.
Most computers these days will come with their fair share of bloatware, i.e. unwanted software that comes preinstalled on the operating system by the developers. While the developers do tend to get paid for including bloatware with their operating systems, there is often no need for it, leading users to question why it’s there and what to do about it.
Microsoft Excel is a handy tool to help businesses keep their data organized… provided it has been used accurately and to its full potential. However, it isn’t uncommon for some people to cram all the information of a record into a single cell and limit the value that Excel has to offer. Once this goes on long enough, it can feel like there’s no fixing it.
Let’s go over how you can, in fact, fix it.
Today’s cars, trucks, and sport utility vehicles are packed with features, many of which heavily lean on technology in order to operate. While these new vehicles and all their new capabilities are certainly appealing to today’s consumer, it needs to be said that one key aspect of technology has not been improved as these vehicles have been innovated upon.
That one key aspect? Security.
You always read that “business has changed”. This is true because society has changed; and technology supports this new normal. More people use their mobile devices for a majority of their communication, their browsing, and a lot more, and it is changing the way business is conducted; it’s just not always easy to separate work use from personal usage. Let’s take a look at some of the ways mobility has changed the way people approach work, and how that shift in perspective has changed business.
Your desktop can often become cluttered with files and programs while you’re going about your workday, and those files and programs will all have desktop icons associated with them. It’s a good practice to clean it up from time to time, but you can get immediate relief from the clutter by adjusting the size of the icons.
The smartphone app ecosystems today are extraordinarily vast. The Google Play store has over 3.5 million apps available, while the Apple App store has over 1.6 million apps. The question becomes, with so many different applications available on these platforms, how can you be so sure that the apps you are downloading to your mobile device are secure? Let’s take a look at mobile app store security and why it’s become more than just a security issue.
Do you remember the “Hello, I’m a Mac, and I’m a PC” commercials that aired from 2006 to 2009? These ads, which featured actors Justin Long and John Hodgeman as Mac and PC, respectively, were put out by Apple to promote their line of computers, highlighting the advantages that Macs had over the PC. One advantage the ads referenced repeatedly was the idea that Macs “don’t get viruses,” something that research conducted by Elastic Security Labs has disproved beyond any doubt.
Artificial intelligence has become a popular topic to discuss in the business world, and like just about any current technology trend, you know Microsoft has to hop on the bandwagon with its own solution. Microsoft’s new AI-powered image generation tools will be integrated into many of their applications moving forward.